Effective Strategies for Handling Network Vulnerabilities
As the digital threat landscape evolves daily, cybercrime continues to impact companies across the United States. By 2027, the cost of cybercrime is expected to reach $23 trillion, forcing businesses to take immediate action to keep their networks and critical data safe.
In addition, recent studies reveal that nearly 61% of companies were impacted by third-party data breaches in 2024, a 48.78% increase over the 41% reported the year prior.
“Leaving network vulnerabilities unpatched is like leaving the doors wide open for attackers, and today’s businesses simply can’t afford that kind of risk anymore,” says Daren Boozer, CEO of NCC Data.
That’s why addressing network security vulnerabilities is crucial for protecting operational stability and preserving brand reputation.
In this article, we’ll examine some common network vulnerabilities, the types of threats they pose, and the proactive steps businesses like yours can take to secure their operations.
Take a Stand Against Network Vulnerabilities with a Trusted Partner
Mitigate cyber vulnerabilities and more when you partner with NCC Data.
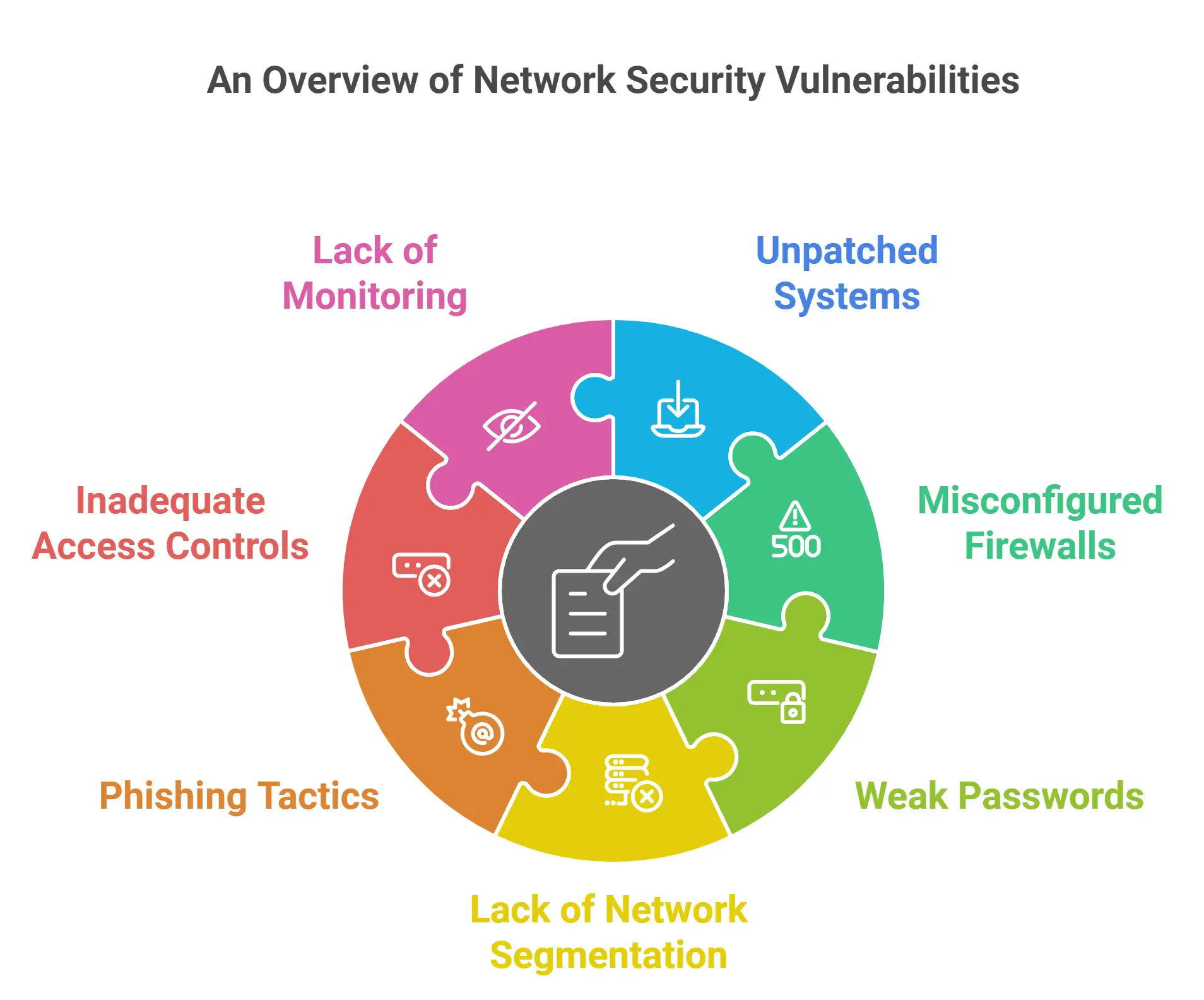
Recognizing the Most Common Network Vulnerabilities
1. Unpatched Systems and Software
Unpatched or outdated software creates one of the biggest cybersecurity vulnerabilities. Without routine updates, organizations leave themselves open to known weaknesses that attackers can easily exploit.
Cybercriminals quickly target older software versions due to widely available information about cyber vulnerabilities. Regular updates and automated patching systems are essential for minimizing this risk and ensuring nothing is overlooked.
2. Misconfigured Firewalls and Security Devices
Firewalls act as a key defense barrier, but misconfigurations can render them ineffective.
Simple errors in firewall setups or network security devices leave entry points that attackers can exploit.
Regular audits and careful configurations are crucial to ensure these devices are operating at full potential, blocking unauthorized access effectively.
3. Weak or Reused Passwords
Despite the availability of sophisticated security measures, weak or reused passwords continue to be a significant issue. Cyber vulnerabilities associated with poor passwords allow attackers to use brute force or phishing attacks to gain unauthorized access.
Enforcing multi-factor authentication (MFA) and strong password policies can drastically lower the chances of unauthorized entry.
4. Absence of Network Segmentation
Network segmentation, which restricts access to different parts of a network, is an essential security measure.
Without segmentation, attackers who breach one area can move laterally across the network. Segmenting network vulnerabilities restricts access, making it more challenging for attackers to infiltrate sensitive areas, while also providing more time for your team to respond.
5. Phishing and Social Engineering Tactics
Phishing and social engineering are among the most successful tactics attackers use to breach networks. Studies show that small businesses are 350% more vulnerable to phishing than larger firms.
Employees who are not trained in cyber threats and vulnerabilities may unknowingly grant access by clicking malicious links or sharing sensitive data. Regular training and simulated phishing exercises can significantly reduce these risks.
6. Inadequate Access Controls and Privilege Management
Excessive access privileges increase the risk of unauthorized access and malicious activity. Adopting the principle of least privilege (POLP) limits users to only what they need, helping to mitigate information security vulnerabilities. Regular access reviews are essential for identifying and managing these risks.
7. Lack of Network Monitoring and Incident Response Plans
Continuous monitoring and a well-structured incident response plan are vital for detecting and managing threats before they escalate.
Many companies lack real-time monitoring, which allows attackers to remain unnoticed for longer periods. Implementing these safeguards ensures that security incidents are quickly identified and addressed, reducing the potential damage
| More articles you might like: |
The High Cost of Overlooking Network Security Vulnerabilities
1. Financial Impact of Data Breaches
Overlooking cyber security vulnerabilities often leads to financial losses from data breaches.
Breached data not only results in direct financial penalties but also has long-term consequences for brand reputation.
With nearly 43% of all breaches targeting small to medium-sized businesses, securing your network against common network vulnerabilities is essential.
2. Disruptions from Ransomware
Ransomware attacks, targeting networks with weak defenses, can bring business operations to a halt. Attackers lock down critical systems, demanding a ransom before allowing restoration. These disruptions result in lost revenue and strained customer relationships.
A multi-layered defense, including backups and anti-ransomware strategies, can minimize these disruptions and keep operations running.
3. Penalties for Compliance Failures
For industries with regulatory standards like HIPAA, PCI-DSS, or GDPR, ignoring network security vulnerabilities can lead to severe penalties, which can reach nearly $15 million.
Even without a breach, the inability to demonstrate compliance can result in costly fines. Proactively addressing vulnerabilities keeps your organization aligned with regulatory standards, avoiding fines and legal issues.
Building a Proactive Defense Against the Different Types of Network Security Threats
1. Conducting Routine Vulnerability Assessments
Regular vulnerability assessments help businesses detect and resolve network security vulnerabilities before attackers can exploit them.
These assessments involve comprehensive audits to spot potential issues across network systems, keeping your business one step ahead of threats.
2. Adopting a Multi-Layered Security Approach
A robust security strategy incorporates multiple defense layers, such as firewalls, intrusion detection, and endpoint security.
Each layer aims to catch threats that may have bypassed previous defenses, creating a comprehensive barrier against attacks.
3. Employee Training in Security Best Practices
Human error remains one of the leading causes of cyber vulnerabilities. Regular training sessions equip your employees with the necessary knowledge to recognize threats, such as phishing or suspicious links, reinforcing your network’s overall defense.
Key Steps for Minimizing Common Network Security Vulnerabilities
| Step | Description | Benefit |
| 1. Patch Management | Regularly update software and systems to address known vulnerabilities. | Reduces the risk of attacks on outdated systems. |
| 2. Configure Firewalls Properly | Ensure firewalls and security devices are correctly set up to block unauthorized access. | Strengthens perimeter security, limiting entry points. |
| 3. Enforce Strong Password Policies | Require strong, unique passwords and implement multi-factor authentication. | Protects against brute force and credential attacks. |
| 4. Network Segmentation | Divide the network into sections to control user access and limit attack spread. | Restricts attacker movement within the network. |
| 5. Conduct Employee Training | Provide ongoing training to help employees identify phishing and social engineering attempts. | Decreases susceptibility to social engineering. |
| 6. Implement Access Controls | Use the principle of least privilege to limit access based on user roles. | Minimizes unauthorized data access. |
| 7. Monitor Continuously | Use real-time monitoring and establish an incident response plan. | Enables quick detection and response to threats. |
Strengthen Your Network’s First Line of Defense with NCC Data
Your network is the foundation of your daily operations. To protect against unauthorized access and data breaches, it’s essential to secure it against any network security vulnerabilities.
NCC Data specializes in building strong, reliable networks for businesses, offering solutions from firewalls to advanced encryption. Our expert approach to network security vulnerabilities helps protect your business from the increasing types of attacks in network security.
NCC Data is proud to support this innovation as a leading local managed IT services provider. For more details on how IT management can transform your business, contact us today to schedule a consultation.
| Discover Trusted Cybersecurity Services Near You: | ||
| Irving | Plano | Fort Worth |
Take the first step towards improving your business’s network security strategy. Contact us today to schedule a free consultation and secure a safer future for your network.
Learn more about omnichannel communication strategies for your company’s virtual workforce at nccdata.com.







